Knowledge base
September 14, 2022
New GIFShell attack targets Microsoft Teams
A cybersecurity consultant has discovered a new attack chain that uses GIF images in Microsoft Teams to execute arbitrary commands on the target’s machine.
The exploit discovered by Bobby Rauch is called “GIFShell” and its main component is a GIF image containing a hidden Python script. This manufactured image is sent to a Microsoft Teams user to create a reverse shell.
By exploiting the legitimate Microsoft infrastructure, an attacker can bypass security controls, make malicious files appear as harmless and exfiltrate critical data. To do all that, the attacker needs the victims to install a “Stager,” an executable file that actually executes the commands embedded in the GIF.
However, the research shows that such installation can be achieved in Microsoft teams themselves through very convincing attachments, without any social engineering or additional exploit from another application.
“This research shows how it is possible to send highly convincing phishing attachments to victims via Microsoft Teams, without any way for a user to pre-screen whether the linked attachment is malicious or not,” Rauch wrote.
Any Teams attachment can be legitimately displayed
Microsoft Teams does indeed support features such as Deep Linking, but it lacks proper cleansing and validation, allowing for potentially insecure URI schemes. Rauch discovered that Teams will try to display files in line even if the app does not know how to display the format (e.g., DLL), thus displaying each attachment as legitimate.
“When a file is uploaded to Microsoft Teams in a message to an authorized user such as a colleague in an Azure organization, Microsoft generates a Sharepoint link to the file, which only the sender and recipient of the team’s message can view,” Rauch wrote. “When a user then clicks send on the Teams message with the attachment, a JSON body in a POST request is sent to a Teams endpoint with the Sharepoint link to the file and various other file attributes.”
The JSON body can be modified by an attacker to allow a remote user to access the Teams attachment despite default restrictions and pass malicious files without any possibility of detection (e.g., in front screens).
The seemingly harmless file can be used for a drive-by download attack:
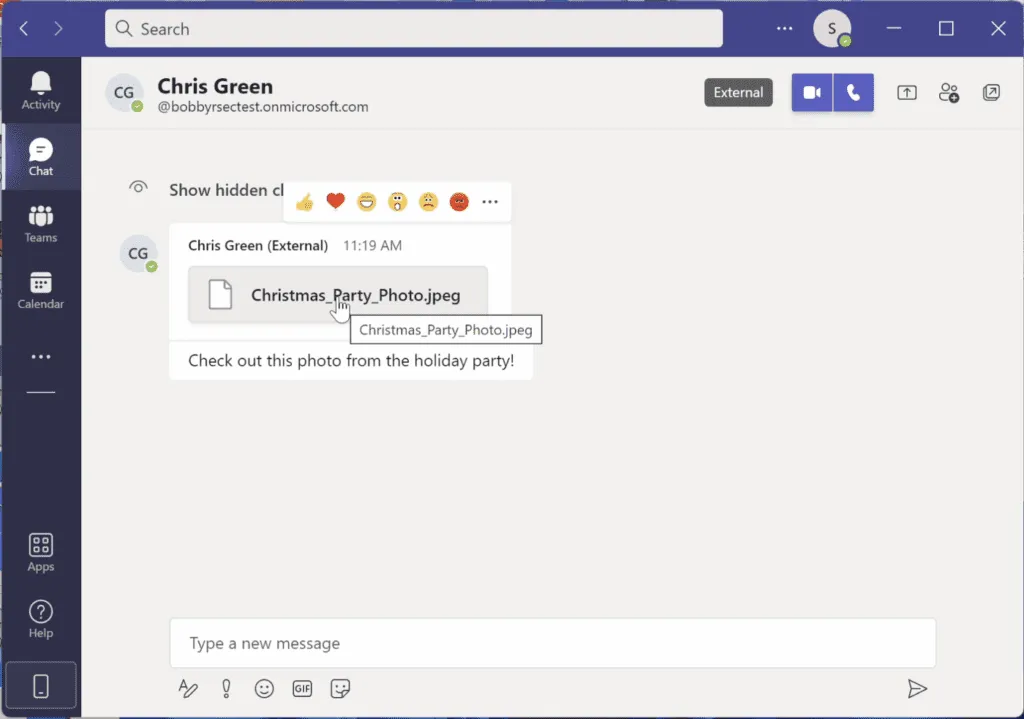
Once installed, the executable can check Microsoft Teams logs to detect and extract base64 encrypted commands. The attackers only need to create their own Microsoft Teams tenant and contact the victims outside their organization, for example through remote meetings or chat. They can then send crafted GIF images that contain malicious commands to be executed by the Stager on the target’s computer. Teams logs contain copies of Teams messages that can be read by all Windows user groups.
The Stager uses the output of the executed commands as the filename (base64 text) of an external GIF embedded in an adaptive map sent to the URL for the incoming webhook connector created for a Teams channel in the attackers’ tenant.
Each time Microsoft’s servers attempt to retrieve the GIF image, it connects to the attacker’s server to deliver the information.
This clever strategy allows attackers to bypass microsoft security tools and secretly exfiltrate data.
How to mitigate GIFShell vulnerabilities
This chain of vulnerabilities was reported to Microsoft in June 2022, but the company decided that the investigation did not meet the “bar for immediate maintenance.
In other words, it’s not a priority for now, but that doesn’t mean it won’t be solved. In the meantime, Rauch recommends the following mitigations:
- Make sure users are trained not to click on attachments from unknown external senders.
- Implement a secure attachment policy in Microsoft Defender for Office 365 to prevent the drive-by download attack.
- Enable SMB signing or disable NTLM completely and make sure there are complex password policies in place to help prevent NTLM attacks.
It should also be noted that Microsoft Teams allows allowlisting of external domains in User Settings (see External Access), so you can theoretically prevent such unwanted communication with arbitrary external organizations.
Red teams and pentesters can attempt to replicate the attack by following Rauch’s requirements and replication steps in his report.
Source: esecurityplanet
Want to know more?

Related
blogs
Tech Updates: Microsoft 365, Azure, Cybersecurity & AI – Weekly in Your Mailbox.