Knowledge base
June 02, 2022
Microsoft plans major security enhancement for unprotected Office 365 tenants
Need for protection (and good security standards) evident in the cloud.
One of the lessons learned from last year’s Hafnium fiasco was that some organizations with on-premises Exchange servers were not managing them properly. This is acceptable if the servers are not exposed to the Internet. It becomes potentially disastrous and a one-way ticket to compromise when they are.
As you may have heard once or twice before, things are different in the cloud. Microsoft manages servers and provides basic maintenance and other matters of server hygiene. Secure servers are good, but compromising user accounts still gives attackers a route to Office 365 tenants. That’s why Azure AD security standards exist.
Default values for Azure AD security for everyone
In October 2019, Microsoft enabled Azure AD Security Defaults for new tenants. In a nutshell, this means that accounts in those tenants use multi-factor authentication (MFA) unless administrators decide otherwise. MFA is good. Even MFA based on text messages is so much better than basic username and password authentication. Combined with conditional access policies, MFA provides a significant barrier against account encroachment.
In a May 25 message, Microsoft announced the extension of Security Defaults to protect tenants created before October 2019. Microsoft says the 30 million tenants currently protected with Security Defaults experience “80 percent fewer compromises than the overall tenant population.” The implementation of MFA is a big step forward. According to Microsoft, “When we look at hacked accounts, more than 99.9% do not have an MFA, leaving them vulnerable to password spraying, phishing and password reuse.” The popularity of password spraying attacks on older email connection protocols such as IMAP4 and POP3 is a major reason why Exchange Online will discontinue basic authentication for these protocols (and five others) starting October 1.
Microsoft says rolling out Security Defaults to older tenants will protect 60 million additional accounts from attack. Given Microsoft’s latest number for Office 365 users (345 million paid seats), that number may seem low. However, it is the number of unprotected accounts in older tenants – many older tenants already use MFA and conditional access policies. The focus is on extending protection to tenants who may not have the IT capabilities to implement better security practices. Microsoft explicitly mentions that they will target “those [tenants] who have not changed security settings since implementation.”
The major rollout
Microsoft says the rollout of Azure AD Security Defaults to unsecured tenants has begun. Initially, they are targeting “clients that are not using conditional access, have not used security standards before, and are not actively using outdated authentication clients.” It is the same way to solve the problem with a simple approach that the Exchange Online team uses to eliminate basic verification: process the easy tenants first, then a little harder, and gradually work through the installed base until you reach the most difficult tenants.
Tenant administrators will receive email notifications of the transition. Starting in late June, administrators will see prompts to enable default security settings when they log in. At this point, they can choose to defer for up to 14 days or choose not to use security standards by changing the settings in the Azure AD management center or Microsoft 365 management center. In Figure 1, you can see that my tenant uses “adaptive MFA,” which is a fancy name for saying that conditional access policies require MFA under certain conditions.
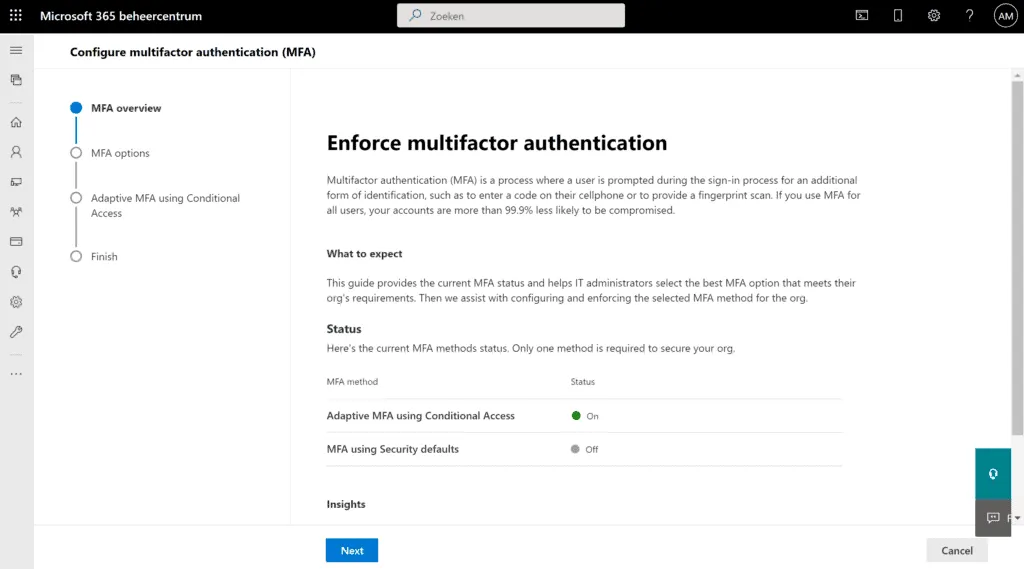
If you enable default security settings, Azure AD will prompt users to sign up for MFA, preferably using the Microsoft Authenticator app on a mobile device as a second authentication factor.
Cloud security is different
On-premises security needs, tactics and techniques are different than those required in the cloud, but if attackers come along, you need to be able to fend them off with the right tools. I think extending Security Defaults to all unprotected Office 365 tenants is an excellent idea that should help people escape the horrors of something like an attack on corporate email. A compromised Azure AD account is bad, and if it’s an administrator account, it can be just as bad as an on-premises server penetrated by something like Hafnium.
Source: practical365
Want to know more?

Related
blogs
Tech Updates: Microsoft 365, Azure, Cybersecurity & AI – Weekly in Your Mailbox.