Knowledge base
August 02, 2023
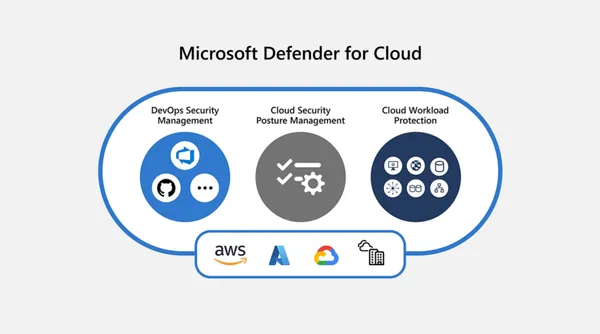
The usefulness of activity logging in Microsoft 365 and implementation
A Chinese hacker who entered a U.S. government account in Microsoft 365 is a wake-up call. It is time to review your current logging practices.
Reappointment and vulnerabilities in Microsoft
On the same day that Microsoft announced the renaming of Azure Active Directory to Microsoft Entra ID, and the company announced that it was tracking an Office/HTML zero-day vulnerability for which no patch was available, the company also released an shocking news fall: A Chinese attacker had targeted some of its customers in the U.S. government.
How the attack took place
By using a stolen Microsoft customer account signing certificate, the hacker misled the authentication process to gain access to government email accounts. How did Microsoft determine that there was a problem?
The role of logging
The company did not. The red signal was given by government customers who had paid for premium logging capabilities and were able to track who had accessed the contents of their mailboxes. The situation highlighted the great importance of logging and knowing what logging functionality comes standard and what is offered through premium services.
Determining the depth of the attack
First, some history. Years ago, there was an API that researchers found would track account activity and expose who had gained access to a mailitem. With a corporate e-mail compromise, you could determine if an attacker had gained access to your network, but you often didn’t know if they opened or had access to certain information or it only appeared that they had.
Insight through logging
When this information came to light, researchers built a tool that would uncover it. It was once said that Microsoft planned to release the so-called “Magic Unicorn” tool that would enable detailed tracking of Office 365 mailbox activity and make it public.
Log access expanded by Microsoft
This also prompted Microsoft to take the bold step of ensuring that every customer has this level of logging available without having to pay for a premium level to gain access. On July 19, 2023, Microsoft announced that it will phase out access to broader cloud security logs for global customers at no additional cost.
Access to log files
Microsoft will begin rolling out these log enhancements in September, but there are ways you can access these log files now and review their information in the meantime. First, use a trial version: if you think a breach has occurred and you don’t have this license, you still want to be aware that the log is available so you can then sign up for a trial.
Conclusion
Would you have known if there had been an attack on your network? Could you have shown that a breach had occurred? Ask yourself these questions and begin to explore what logging options you want to include in your own resources.
If you need help implementing these logging capabilities or have questions about your network security, don’t hesitate to contact the Alta-ICT team. We are ready to support you.
If you need help implementing these logging capabilities or have questions about your network security, please do not hesitate to contact the team at ALTA-ICT. We are ready to support you.
Want to know more?

Related
blogs
Tech Updates: Microsoft 365, Azure, Cybersecurity & AI – Weekly in Your Mailbox.