Knowledge base
August 27, 2022
Hackers have found a new way into your Microsoft 365 account
Cybercriminals brutally force into Azure AD accounts without MFA
Russian state-sponsored threat actor Cozy Bear (also known as APT29 or Nobelium) is deploying new tactics to sneak into Microsoft 365 accounts in an attempt to steal sensitive foreign policy intelligence.
This is according to a new report from cybersecurity firm Mandiant, which claims that Cozy Bear uses three techniques to carry out (and hide) the attacks:
- Disable Purview Audit before using a compromised email account
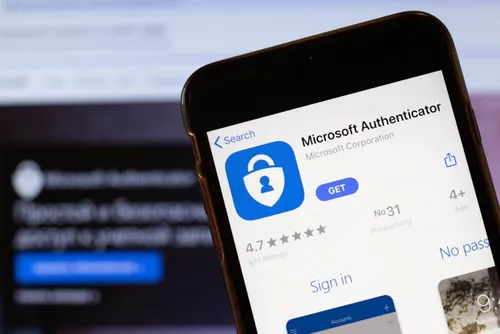
- Brute-forcing Microsoft 365 passwords who have yet to sign up for multi-factor authentication (MFA)
- Covering their tracks by using Azure Virtual Machines through compromised accounts or by purchasing the service
New Microsoft 365 attack
Purview Audit, the researchers remind, is a high-level security feature that logs when a person accesses an email account outside the program (via the browser, Graph API or through Outlook). This allows IT departments to manage all accounts and ensure that there is no unauthorized access.
However, APT29 is well aware of this feature and makes sure you disable it before accessing an email.
The researchers also discovered that Cozy Bear was abusing the self-subscription process for MFA in Azure Active Directory (AD). When a user tries to log in for the first time, they must first enable MFA for the account.
Threat actors aim to circumvent this feature by brutally forcing accounts that have yet to enroll in the advanced cybersecurity feature. They then complete the process in place of the victim and grant unabated access to the target organization’s VPN infrastructure and thus the entire network and endpoints.
Finally, Azure’s virtual machines already contain Microsoft IP addresses, and because of the fact that Microsoft 365 runs on Azure, IT teams struggle to distinguish regular from malicious traffic. Cozy Bear can further hide its Azure AD activity by combining ordinary URLs of application addresses with malicious activity.
The likelihood of regular users being targeted by the threat group is probably relatively low, but large companies should be alert to the attack vector, which can be used to target high-profile executives and others with access to sensitive information.
Source: tech radar
Want to know more?
Related
blogs
Tech Updates: Microsoft 365, Azure, Cybersecurity & AI – Weekly in Your Mailbox.