Knowledge base
August 07, 2021
A smart phishing campaign targets Office 365 users
Microsoft warns of an ongoing, “sneaker than usual” phishing campaign targeting Office 365 users.
The phishing emails
The phishers use different themes as bait and the emails are sent from email addresses of different top-level domains.
The sender addresses include variations of the word ‘referral’, e.g., zreffertalt.com.com, refferal.net, irefferal.com, and the like. The emails are made to look like they’re referencing a shared document stored on Microsoft SharePoint, a web-based collaboration platform that integrates with Microsoft Office, and they include Microsoft branding.
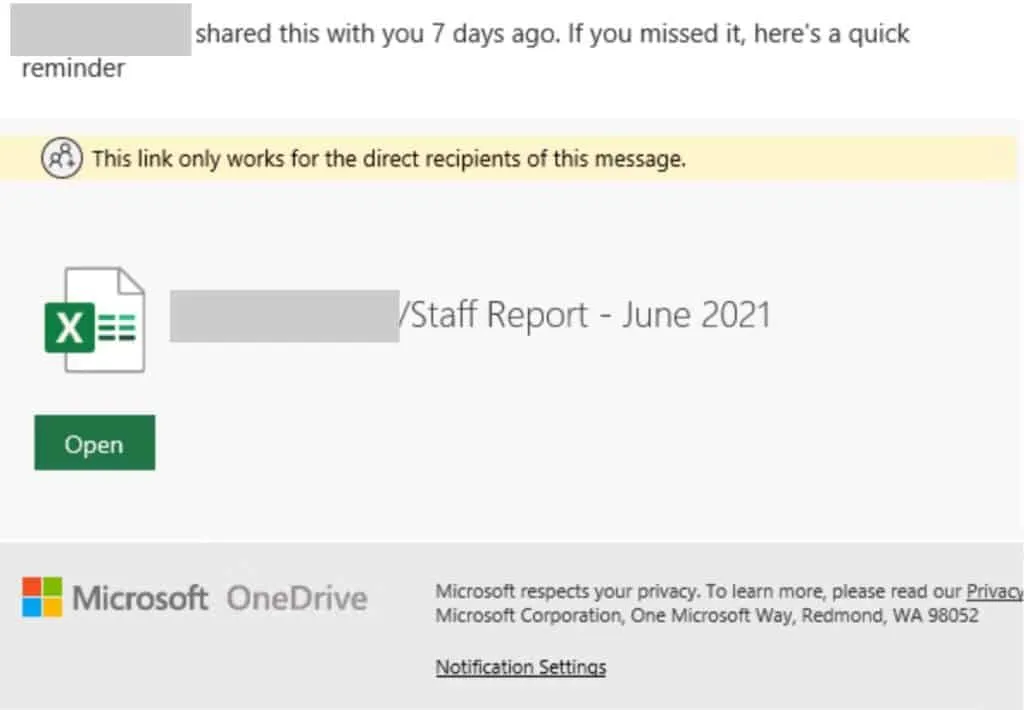
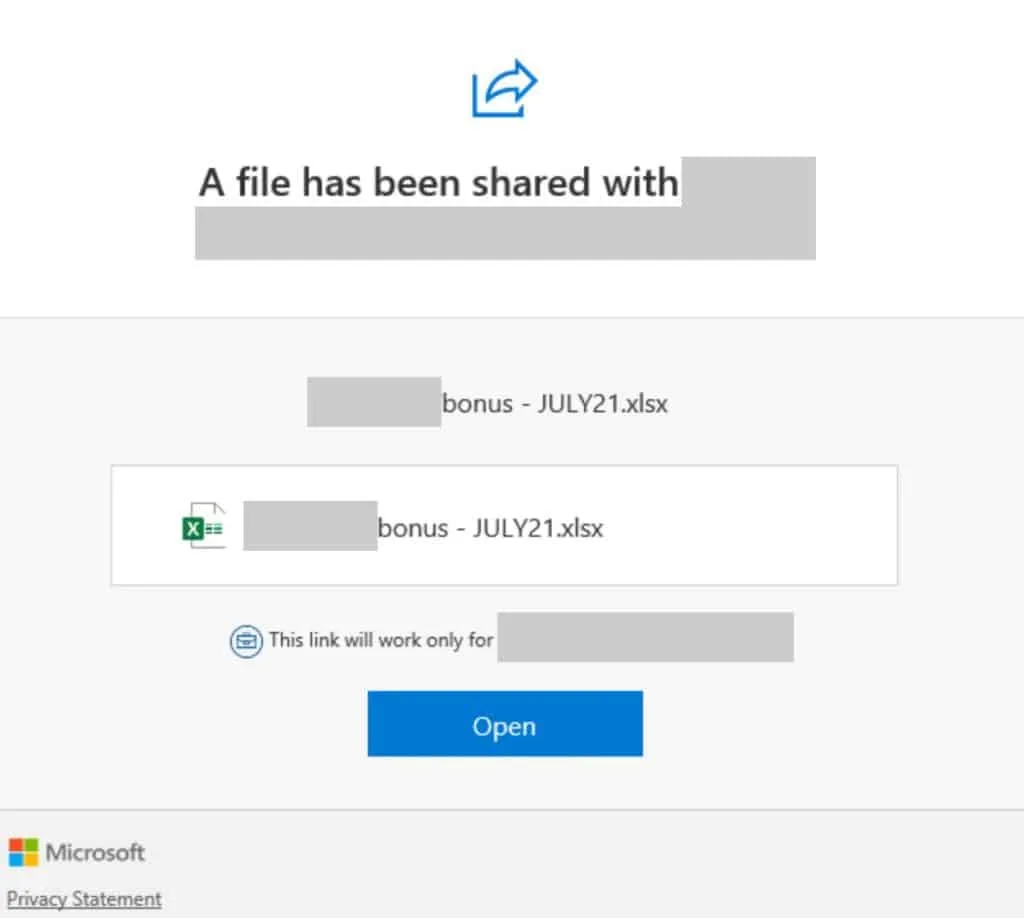
The fake documents are supposedly employee reports, ‘price book changes’, contain information about bonuses, and so on. But clicking the link will take users to an Office 365 themed phishing page.
“The emails contain two URLs with malformed HTTP headers. The primary phishing URL is a Google repository that points to an AppSpot domain that the user must log in to before finally serving another Google User Content domain with an Office 365 phishing page,” Microsoft noted.
“The second URL is located within the notification settings and leads to a compromised SharePoint site that the attackers use to add legitimacy to the attack. Both URLs require login to proceed to the last page, bypassing many sandboxes.”
Using Google and Microsoft’s cloud infrastructure host phishing pages is just one of the ways phishers try to circumvent gateways and email security solutions. This campaign apparently uses other tricks, but Microsoft hasn’t specified which ones.
The company has shared an advanced hunting query that defenders can use to prevent the emails from being delivered.
Source: helpnet security
Want to know more?

Related
blogs
Tech Updates: Microsoft 365, Azure, Cybersecurity & AI – Weekly in Your Mailbox.