Knowledge base
July 27, 2023
FIDO2 Support & Condition Access Policy Now Available on Azure AD
To protect the country’s infrastructure and improve cybersecurity, Executive Order 14028 and Office of Management and Budget Memo M-22-09 took a strong position to require phishing-resistant authentication for all federal agencies. The M-22-09 memo also specifies two standard-based authentication protocols that meet phishing-resistant requirements, namely FIDO2/WebAuthn and PIV smart cards.
PIV Smartcards in the Microsoft Ecosystem
In the Microsoft ecosystem, PIV smart cards have long been supported for desktop systems on Windows and macOS. Recently, the company announced a big win for government agencies and organizations already using smart cards by expanding support for PIV smart cards on mobile devices with YubiKeys.
Considerations for FIDO2 Authentication.
If you have read Joe Scalone’s opinion on FIDO2 for the federal government, you may be wondering about Microsoft customers who do not have the PKI infrastructure to support smart card issuance, or government users who are not eligible for PIV. Or perhaps about customers who want to move to more modern FIDO2-based authentication and need support on mobile devices. These are important questions.
Support for YubiKeys on Mobile Devices.
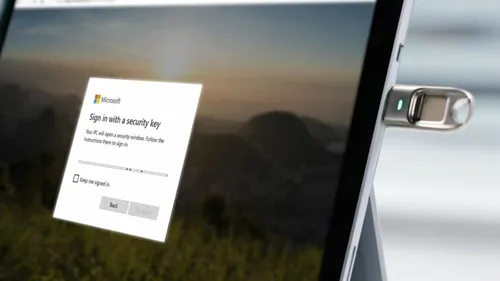
Entra ID (Azure AD) has been supporting the use of YubiKeys for FIDO2 passwordless login since 2021, and customers have been waiting since then to log in with their YubiKey from their mobile devices. Now the tide is beginning to turn. Microsoft recently announced general availability for using FIDO2 security keys with Safari, and this new support goes beyond desktops and includes iPhones and iPads.
Strengthening Authentication with Condition Access Policies
Every organization should now be well on its way to a passwordless and Zero Trust journey. With support for mobile, organizations can now take their journey a step further.
Condition Access Policy Authentication Strengths was also announced by Microsoft this spring, giving customers the flexibility to require PIV or FIDO2 everywhere except for edge cases where the protocols are not yet supported. This enables organizations to move closer and closer to a modern passwordless end state, where end users are no longer allowed to use phishable authentication methods when accessing applications.
Starting to Use YubiKeys with Safari
If your YubiKey does not have a PIN set yet, you must set a PIN first, because Safari does not support PIN setting. On iOS, there are no convenient options to do this. The following steps use macOS desktop with Yubico Authenticator to set the PIN, but there are other options, such as using YubiKey Manager or Chrome on macOS. Check Yubico’ s website for more information.
Source: Yubico
Want to know more?
Related
blogs
Tech Updates: Microsoft 365, Azure, Cybersecurity & AI – Weekly in Your Mailbox.