
Knowledge base
January 03, 2024
Cybersecurity Strengthened: New in Phishing-Resistant Authentication
In a world where digital security is becoming increasingly crucial, Microsoft’s recent announcement about strengthening phishing-resistant authentication is an important step forward. These developments are not only vital for compliance, but also crucial for the security of organizations and users who rely on digital identities.
Key Developments
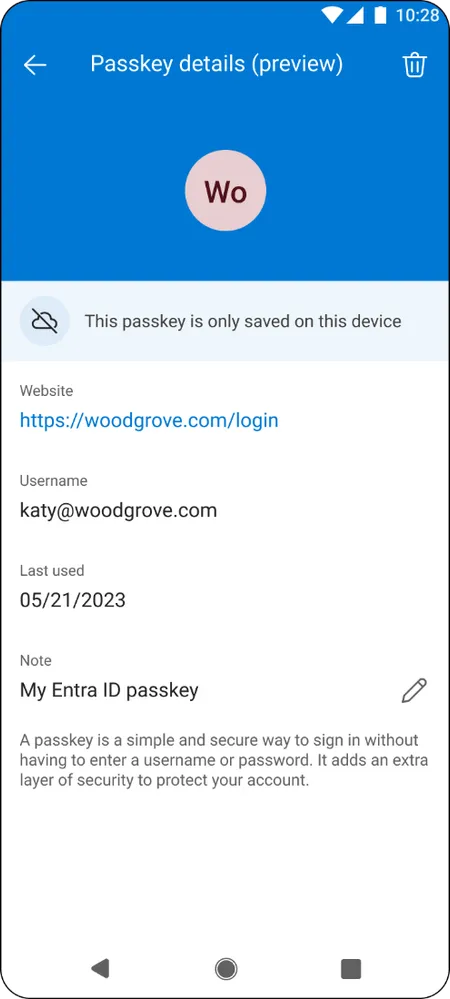
- Phishing-Resistant Passkey Support: Microsoft Authenticator announces support for phishing-resistant passkeys, a cost-effective and secure form of authentication for anyone with the Authenticator app.
- FIPS 140-3 Compliance: On both Android and iOS, Microsoft Authenticator is now compliant with the Federal Information Processing Standard (FIPS 140-3), ensuring a higher level of security and compliance.
- Enhanced Configuration Options: Certificate-based Authentication (CBA) deployment has grown significantly, and Microsoft continues to invest in cloud-based CBA with new capabilities that offer more customization of authentication policies.
- FIDO2 Support for iOS and macOS: Support for FIDO2 authentication on iOS and macOS web browsers is now in public preview, allowing users with Microsoft Authenticator or Intune Company Portal on macOS to log in to Microsoft applications with a FIDO2 security key.
Future Vision and Collaboration
Microsoft is committed to a “Secure by design, Secure by default” approach and works closely with government agencies and security experts to strengthen collective defenses against cyber threats. These efforts are part of Microsoft’s Secure Future Initiative and include the automatic rollout of Conditional Access policies.
Security Plus: Phishing Resistance & Conditional Access
In addition to implementing phishing-resistant authentication methods, it is crucial to combine them with conditional access for a robust layer of security. Conditional access ensures that access to corporate resources depends not only on the accuracy of login credentials, but also on additional context such as the user’s location, the device used, and the security status of that device.
This is especially important given the reality of MFA (Multi-Factor Authentication) bypass techniques. Although MFA is a strong barrier against unauthorized access, there are sophisticated attack techniques that can bypass MFA. For example, attackers may use phishing campaigns specifically designed to intercept MFA codes or techniques such as man-in-the-middle attacks to bypass authentication.
By integrating conditional access, organizations can enforce dynamic security policies that account for various risk factors, reducing the likelihood that attackers can circumvent these security measures. This provides a more adaptive and context-aware approach to cybersecurity, tightly controlling access to sensitive information and systems based on real-time assessments of potential security risks.
Conclusion
Microsoft’s recent improvements in phishing-resistant authentication highlight the importance of advanced security in today’s digital world. By strengthening authentication processes and adhering to high security standards, Microsoft is contributing to a more secure digital future for organizations and individual users.
To take the security of your digital environment to the next level, combining phishing-resistant authentication with conditional access is essential. This approach ensures that only authorized users can access your systems, and only under the right circumstances.
Want to know more about how to implement these advanced security measures within your organization? If so, please contact ALTA-ICT. Our team of experts is ready to support you in strengthening your cybersecurity with the latest solutions from Microsoft.
Want to know more?
