Knowledge base
November 10, 2020
Microsoft Teams phishing attack targets Office 365 users.
Up to 50,000 Office 365 users will be targeted by a phishing campaign that claims to notify them of a “missed chat” from Microsoft Teams.
Researchers warn of a phishing campaign posing as an automated message from Microsoft Teams. In reality, the attack is intended to steal the login credentials of Office 365 recipients.
Teams is Microsoft’s popular collaboration tool, which has grown in popularity among external employees during the pandemic, making it an attractive brand for attackers to pose. This particular campaign has been sent to between 15,000 and 50,000 Office 365 users, according to investigators from Abnormal Security on Thursday.
“Because Microsoft Teams is an instant messaging service, recipients of this notification may be more likely to click on it, so they can quickly respond to any message they think they missed based on the notification,” researchers said in an analysis thursday.
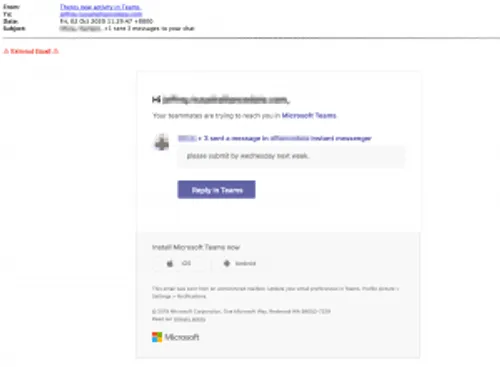
The first phishing email contains the name “There’s new activity in Teams,” making it look like an automatic notification from Microsoft Teams.
As seen in the image below, the email tells the recipient that their teammates are trying to reach them, alerting them that they missed Microsoft Team chats, and showing an example of a teammate chat asking them to submit something before Wednesday of next week.
Erin Ludert, data scientist at Abnormal Security, told Threatpost researchers that attackers here are using more of a “spray” tactic because the employee referenced in the chats does not appear to be an employee of the company that received the attack.
To respond, the email encourages the recipient to click the “Respond in Teams” button. However, this leads to a phishing page.
“In the body of the email there are three links that appear as ‘Microsoft Teams’, (contact) has sent a message in instant messenger ‘and ‘Respond in teams’, according to researchers. If you click on one of these, you’ll find a fake website that mimics Microsoft’s login page. The phishing page asks the recipient to enter his email address and password. “
Researchers said the phishing landing page also looks convincingly like a Microsoft login page, with the beginning of the URL containing “microsft teams.” If recipients are convinced to enter their Microsoft credentials on the page, they unknowingly surrender them to attackers, who can then use them for a variety of malicious purposes, including taking over accounts.
The ongoing pandemic has raised concerns about cyber attackers using business-friendly collaboration brands such as Microsoft Teams, Zoom and Skype. In May, a convincing campaign posing as reports from Microsoft Teams to steal employees’ Office 365 login credentials circulated, with two separate attacks targeting as many as 50,000 different Teams users.
Microsoft is at the top when it comes to impersonating hackers – with Microsoft products and services occurring in nearly a fifth of all global brand phishing attacks in the third quarter of this year. Attackers also use advanced tactics, including visual CAPTCHAS to target Office 365 users and token-based authorization methods.
To respond, the email encourages the recipient to click the “Respond in Teams” button. However, this leads to a phishing page.
“In the body of the email there are three links that appear as ‘Microsoft Teams’, (contact) has sent a message in instant messenger ‘and ‘Respond in teams’, according to researchers. If you click on one of these, you’ll find a fake website that mimics Microsoft’s login page. The phishing page asks the recipient to enter his email address and password. “
Researchers said the phishing landing page also looks convincingly like a Microsoft login page, with the beginning of the URL containing “microsft teams.” If recipients are convinced to enter their Microsoft credentials on the page, they unknowingly surrender them to attackers, who can then use them for a variety of malicious purposes, including taking over accounts.
The ongoing pandemic has raised concerns about cyber attackers using business-friendly collaboration brands such as Microsoft Teams, Zoom and Skype. In May, a convincing campaign posing as reports from Microsoft Teams to steal employees’ Office 365 login credentials circulated, with two separate attacks targeting as many as 50,000 different Teams users.
Microsoft is at the top when it comes to impersonating hackers – with Microsoft products and services occurring in nearly a fifth of all global brand phishing attacks in the third quarter of this year. Attackers also use advanced tactics, including visual CAPTCHAS to target Office 365 users and token-based authorization methods.
Source: threatpost
Want to know more?
Related
blogs
Tech Updates: Microsoft 365, Azure, Cybersecurity & AI – Weekly in Your Mailbox.