Knowledge base
January 14, 2024
Guide to Microsoft Defender for Identity Dashboard
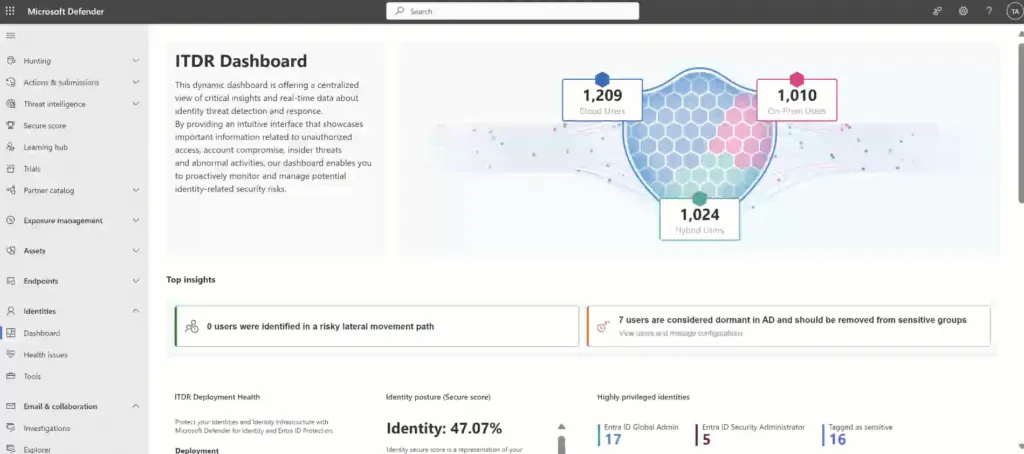
The Microsoft Defender for Identity Dashboard is a crucial tool in the arsenal of modern cybersecurity. It provides in-depth insights and real-time alerts to protect organizations from identity-related cyber attacks.
Key Features of the Dashboard
The dashboard plays a key role in identifying and responding to suspicious activity. It provides comprehensive analysis of user behavior, network activity and potential threats, which is essential for proactively securing identities within an organization.
Real-time Alerts and Analyses
With real-time alerts and detailed analytics, the dashboard helps IT professionals respond quickly to suspicious activity and vulnerabilities.
Learning and Detection Capabilities
The dashboard adapts to each organization’s unique environment, thanks to advanced learning and sensing technologies.
Integration with Cybersecurity Strategy
Defender for Identity Dashboard is an indispensable part of a holistic cybersecurity strategy. It not only helps monitor the security of identities, but also provides valuable insights for strengthening the organization’s overall security posture.
Advanced Analysis and Detection
One of the most powerful aspects of Microsoft Defender for Identity is its ability to recognize complex attack patterns and suspicious activity that indicate advanced threats. This section dives deeper into the machine learning and behavioral analysis technologies that Defender for Identity uses to detect anomalies, such as unusual login attempts and lateral movement attempts within the network.
Implementation Strategies
Successful implementation of Defender for Identity requires a thoughtful approach. This section provides step-by-step guidelines for planning and executing a deployment, including setting up detection rules, configuring access rights and integrating Defender for Identity with existing IT infrastructures.
Integration with Other Microsoft Security Solutions
Defender for Identity does not work in isolation but is an integral part of the broader Microsoft 365 Defender ecosystem. This section highlights how Defender for Identity works with other solutions such as Microsoft Defender for Endpoint and Microsoft Cloud App Security to provide a holistic security strategy that seamlessly integrates identity protection with endpoint and application security.
Case Studies and Use Scenarios.
By sharing real-world examples of how organizations have used Defender for Identity to fend off complex threats, this section provides practical insight and evidence of the solution’s effectiveness. Various scenarios are discussed, from detecting insider threats to stopping advanced persistent threats (APTs).
Best Practices and Optimization
Maximizing the value of Defender for Identity goes beyond installation and configuration. This section offers recommendations for fine-tuning detection rules, optimizing alert settings and conducting regular security audits to ensure that an organization’s security posture is continuously improved.
Future Developments
Finally, this section looks ahead to future updates and planned features for Defender for Identity, based on Microsoft’s roadmap. This includes new detection methods, improved integrations with other products and services, and developments in AI and machine learning that will enhance detection capabilities.
Conclusion
The comprehensive capabilities of Microsoft Defender for Identity Dashboard make it an essential tool for any organization looking to strengthen its security against identity-related threats.
Want to know more?

Related
blogs
Tech Updates: Microsoft 365, Azure, Cybersecurity & AI – Wekelijks in je Mailbox.